Written by Merche Martínez
Index
What is phishing?
Phishing
is the term used to describe a type of fraud aimed atfishing for confidential information, such as credit card numbers, passwords, bank account details or other personal data of the victims. The reason for their success is that they appear reliable and trustworthy to users.
There are different versions of this scam, but the modus operandi usually follows the same patterns. Scammers 
One of the ways to carry out this technique is by means of a phone call or SMS where the fraudsters pretend to be a bank or any trustworthy company to warn you that they need some confidential data with any excuse that can convince the victim.
But the most used way is by e-mail. Phishing e-mails come in various forms:
- You can pretend it comes from a financial institution, a well-known company or even social networks.
- The e-mail can pretend to come from a contact in your e-mail address book.
- You may be asked to make a phone call. When you make the call a person or an audio response unit waits to get your account number, personal identification number, password or other valuable personal data.
- They may include official-looking logos and other information taken directly from legitimate websites, and may include convincing details about your personal history. Fraudsters obtain this information from social networks.
- They may include links to spoofed pages where you are asked to provide personal information.
Examples of phishing
Confirm access data
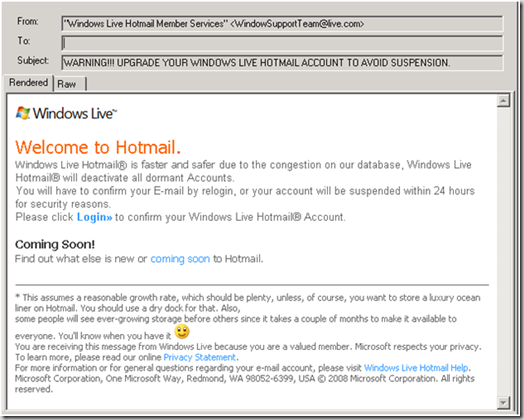
This is one of the best known cases, it consists of an e-mail from Hotmail informing us that we must confirm that we are active users by entering our access data, otherwise our account will be temporarily deactivated.
Update data in banks
This case is one of the most dangerous, it consists of an e-mail that apparently comes from our financial institution. Supposedly they ask us for our account information for security reasons, but in other cases it is also justified as maintenance of the entity, to improve the service provided, surveys, confirmation of your identity or any other excuse.
Once these data have been obtained, the fraudsters have access to all our savings, they can directly empty our account or make online purchases.
How to recognize a phishing message?
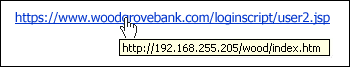
As I mentioned earlier, in the case of phishing by e-mail, a link is included to a web page that apparently belongs to our bank or trusted company, but which is not. It is a forgery and the best way to find out is to look at the real address of the link. To do this we must put the cursor over the link and see the actual address to which the link points.
In this example it is clear that the real address of the link does not correspond to the URL displayed.
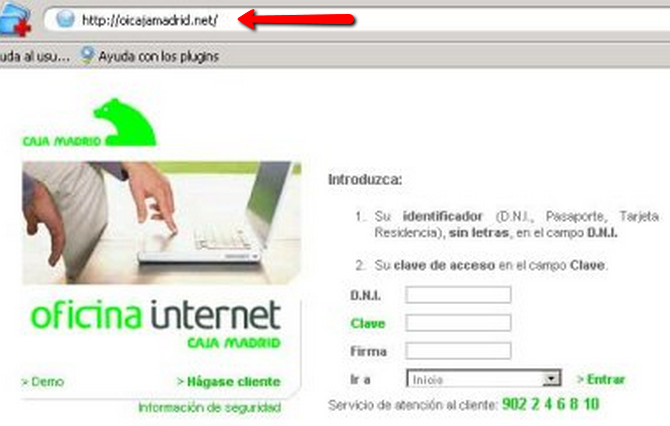
We can also check the veracity of the website by looking at the URL that appears in the address bar of our browser. Sometimes there are fake pages whose domain is very similar to the real one and it is difficult for the user to be aware of the danger of entering confidential data on that site. This practice is known as cybersquatting. A well-known example was the one suffered by the bank Caja MadridThe way to access was http://www.cajamadrid.es and to navigate safely https://oi.cajamadrid.es. The fraud was carried out under the domain http://oicajamadrid.net/, at first sight it was exactly the same as the real one.
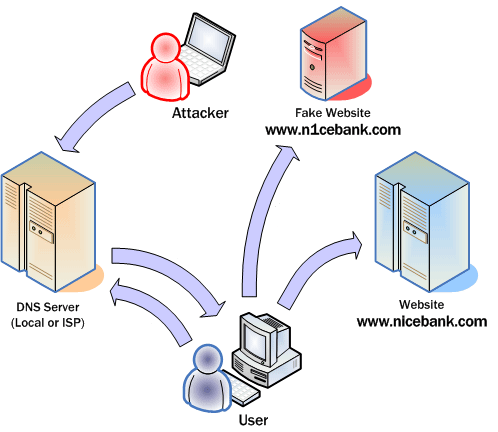
Pharming
It is an advanced technique for phishing. This technique consists of modifying the domain name resolution system (DNS) to lead the user to a fake web page. The address we enter in the browser is converted into a numerical IP address, which is handled by the DNS servers.
In this case the user is more unprotected since the address he is entering is correct.
The term pharming comes from farm, which means farm in English. When DNS server data is modified, all users of that service become victims of the spoofing, which is interpreted as a victim farm.
Tips to protect yourself from phishing
- Do not provide personal data by e-mail. Companies and banks never ask for financial data by this means.
- If you doubt the veracity of an e-mail, do not click on the link, but instead type the address directly into your browser. And if we continue to have doubts, it is advisable to check the veracity of the e-mail with the sender’s financial institution or company.
- Before entering data on a website, make sure that it is a secure address. To be secure, it must use the https:// protocol and display a small closed padlock in the address bar of the browser.
- Periodically review bank accounts to detect irregular transfers or transactions.
- If we think we may have been victims of phishing, we should immediately change all passwords and notify the company or bank of the incident.
- Use a good antivirus and keep it updated.
How do I report that I have been a victim of phishing?
To denounce these practices, we rely on the technological investigation brigade of the national police (BIT).
According to the Penal Code, the penalty could be up to three years imprisonment, plus a fine, and the return of the swindled money, with interest, and, if applicable, the fees accrued for the corresponding conviction in costs of the private prosecution.